TECHNOLOGY
How CASB Works to Secure Your Cloud Data

Key Takeaways:
- CASB serves as a pivotal security control point for organizations using cloud services.
- CASB operates through various methods: visibility, compliance, data security, and threat protection.
- The adaptability of CASB solutions allows for customized applications based on specific organizational needs.
- Choosing the right CASB requires careful evaluation of features, compatibility, and strategic goals.
- Future developments in CASB will likely incorporate advancements in AI and ML to provide even more robust security.
Table of Contents:
- Introduction to Cloud Security
- What is CASB?
- How CASB Operates to Protect Data
- Core Features of CASB Solutions
- The Benefits of Implementing a CASB
- CASB Deployment Models
- Considerations When Choosing a CASB
Introduction to Cloud Security
The migration to cloud computing has been a strategic move for organizations aiming to scale resources, improve flexibility, and promote collaboration. With this migration comes securing sensitive data outside the traditional perimeter-based defenses. As organizations relinquish direct control of their information assets, the spotlight shines on innovative security measures that safeguard data in transit and at rest across diverse cloud environments.
To address these concerns, cloud security leverages encryption techniques, identity and access management (IAM) policies, and advanced threat detection systems to protect data from unauthorized access and breaches. Cloud security testing strengthens these defenses even further by identifying and plugging any vulnerabilities in the cloud.Additionally, compliance with industry standards and regulations is critical to cloud security, helping assure stakeholders of their data’s integrity and confidentiality. Companies also employ multi-factor authentication and regular security audits as a comprehensive strategy to fortify their cloud environments against emerging cyber threats.
What is CASB?
Cloud Access Security Brokers (CASB) have emerged as vital components in the cloud security landscape. A CASB is an intermediary between cloud service users and providers, ensuring that the enterprise’s security policies govern the interaction. It acts as a gatekeeper, allowing the organization to extend the reach of its security policies beyond its infrastructure and into the cloud, creating a secure bridge into the digital cloud frontier.
CASBs provide granular visibility into and control over user activities and sensitive data across multiple cloud services, helping to combat issues like data leakage, non-compliant data storage and access, and unauthorized sharing. They enforce security policies by auditing and real-time monitoring of activities, applying context-aware security measures such as encryption, tokenization, and access controls based on user, location, and device. Furthermore, CASBs can identify and mitigate cloud threats such as malware and ransomware, making them indispensable in comprehensive cloud security strategies.
How CASB Operates to Protect Data
CASBs secure cloud data through a variety of mechanisms. Visibility is foundational, granting administrators insights into cloud application use and user engagement patterns. Compliance is another crucial element, with CASBs helping organizations meet regulatory standards by enforcing data governance practices. For direct data protection, CASBs deploy encryption and tokenization strategies, and they also apply contextual access control to ensure the right people have the right level of access. Lastly, CASBs offer threat protection by identifying and mitigating risks from malware and insider threats.
Additionally, CASBs can integrate with existing security solutions, providing a holistic approach to cloud security that enhances overall cybersecurity frameworks. They offer continuous monitoring and assessment of the security posture of cloud environments, ensuring that vulnerabilities are identified and addressed swiftly. Using advanced analytics, CASBs can detect abnormal behavior that could indicate a security incident, allowing for rapid response and mitigation to prevent potential data breaches or system compromises.
Core Features of CASB Solutions
A comprehensive CASB solution provides a suite of features that offer a multi-layered security approach. Some of these features include:
- Real-time Monitoring: Continuous tracking of user activities and transactions within cloud applications to detect potential security concerns.
- Data Loss Prevention (DLP): Policies and capabilities to prevent sensitive information from leaking outside the corporate cloud environment.
- Cloud Security Posture Management (CSPM): A set of services for continuous discovery of cloud assets, identification of misconfiguration, and the enforcement of best practices in cloud security.
- Advanced Threat Detection: Utilizing behavioral analytics and threat intelligence to recognize and counteract sophisticated cyber threats that target cloud platforms.
The Benefits of Implementing a CASB
Embracing CASB technology offers many benefits, from improved compliance and governance to more robust protection against external and internal threats. By integrating a CASB, organizations gain enhanced visibility over cloud data, more effective control mechanisms, and rich insights into cloud threats—all combined into a solution that can be wielded to secure various cloud services and applications.
This improved oversight allows companies to comply with industry regulations and enforce their internal security policies more rigorously. Furthermore, a CASB facilitates smoother audits by providing comprehensive logs and reports detailing cloud usage and security incidents. Ultimately, deploying a CASB enables organizations to safely harness the power of cloud computing while mitigating the risks associated with data breaches and cyber-attacks.
CASB Deployment Models
CASBs can be deployed in multiple configurations to suit distinct organizational needs and cloud architectures. These include on-premises appliances, cloud-based services, or hybrid models. Each deployment model offers specific advantages, whether it’s the robust control and customizability of on-premises implementations or the scalability and ease of management characteristic of cloud services.
Hybrid models combine the best of both worlds, providing flexible solutions that allow organizations to leverage the immediate scalability of the cloud while retaining specific critical data under more stringent on-premises security. This variety in deployment options ensures businesses can align their CASB strategy with their overall IT infrastructure and security requirements. Additionally, regardless of the deployment model chosen, CASBs integrate seamlessly into existing security systems, enhancing overall protection without requiring major overhauls.
Considerations When Choosing a CASB
Selecting a CASB is a strategic decision requiring careful deliberation. Key factors to consider include compliance with relevant standards, the ability to cover all cloud apps and resources utilized by the organization, ease of integration with existing security tools, the sophistication of the analytical features provided, and the overall cost of ownership. Organizations must also consider the support and services the CASB vendor offers, ensuring they choose a partner that aligns with their long-term security and technological roadmaps.
TECHNOLOGY
How to Reach betechit.com Contacts Effectively

In the digital age, being able to reach a website’s customer support or contact representatives is vital. Whether you’re a customer, business partner, or tech enthusiast, having access to direct communication can resolve problems quickly and help build stronger trust.
The platform betechit.com has emerged as a digital technology hub offering a range of services or content (depending on its exact nature, which may vary), and users often search for “betechit.com contacts” to find accurate ways to reach out for support, questions, collaborations, or complaints.
This article explores all possible ways you can reach out to betechit.com contacts, how to communicate effectively, and what to expect from different contact channels.
Why You Might Need to Contact betechit.com
There are a variety of reasons why users or partners might seek contact with betechit.com, including:
Technical support issues
Account or login concerns
Content disputes or copyright questions
Partnership or advertising inquiries
Clarification about services, tools, or products
Business development or investor interest
User feedback or bug reporting
Understanding your purpose helps you choose the right channel and approach.
Searching for Official Contact Channels on betechit.com
The first step is to identify official sources. You don’t want to waste time with unverified email addresses or suspicious forms. Here’s what to look for on the website:
Contact Us Page:
Most websites have a dedicated “Contact Us” page—often linked in the footer or header. It usually contains contact forms, emails, or social media links.
About Page or Team Page:
Sometimes, the About or Team section may list individual contacts for specific departments, such as PR or tech.
Privacy Policy or Terms of Service:
These legal pages often contain contact details for legal notices, complaints, or data inquiries.
If betechit.com has an active blog or news section, the author bios might also include email addresses or professional social links.
Email Contact for betechit.com
Email remains one of the most reliable and formal ways to reach online platforms. If betechit.com provides an official email, ensure it’s listed directly on their site and not found on unreliable third-party pages.
When writing a professional email to betechit.com, be sure to:
Use a clear subject line (e.g., “Tech Support Request – Account Issue”)
Introduce yourself and your reason for writing
Be specific and polite
Include relevant details (order number, user ID, URL, etc.)
Attach any supporting documents or screenshots
Emails should ideally be responded to within 24 to 72 hours, depending on the nature of the query.
Using Contact Forms on betechit.com
Many modern websites use embedded contact forms. These forms are often found on the Contact Us or Support page. They allow visitors to fill in fields such as:
Name
Email address
Subject
Message or description of issue
Forms are useful because they route inquiries to the correct department automatically. However, users should ensure they receive a confirmation email that their message was received.
Social Media as a Contact Option
If you’re unable to find email support, social media may be the next best thing. Websites like betechit.com often maintain official profiles on platforms like:
Facebook
Twitter (X)
LinkedIn
Instagram
YouTube
TikTok (if relevant)
Most of these platforms offer direct messaging features. Social channels are particularly effective for:
Public inquiries
Real-time responses
Community engagement
Just make sure you are contacting a verified or official page—not impersonators.
Contacting Through Live Chat or Bots
Some tech websites, especially those dealing with tools or services, may offer live chat functionality. This can usually be accessed via a chat bubble in the lower right corner of the screen.
Live chat is best for:
Quick troubleshooting
Billing and account questions
Guidance on how to use site features
Bots may initially handle the conversation, but many systems escalate to human agents if the issue is complex.
Who Should You Contact at betechit.com?
Depending on your purpose, here’s a general breakdown of whom you should be reaching out to:
Customer Support for account-related issues
Sales Department for business or product-related queries
Marketing Team for partnership, advertising, or PR
Technical Support for bugs, crashes, or usability questions
Legal Team for copyright, privacy, or dispute resolution
Large platforms like betechit.com typically segment their support in this way for faster resolution.
Response Time Expectations
The time it takes to get a reply can vary widely depending on the platform’s size, support infrastructure, and current demand.
General guidelines:
Email: 24–72 hours
Live Chat: Instant to 30 minutes
Contact Forms: 1–3 business days
Social Media DMs: Same day to 2 days
Make sure to follow up politely if you do not receive a response within a reasonable timeframe.
What to Include in Your Inquiry
To improve your chances of getting a helpful response, be sure to include:
A detailed description of your concern
Specific URLs or pages (if relevant)
Screenshots or attachments
Previous correspondence (if following up)
Your contact information
Time/date of issue (if applicable)
Organized, polite messages often receive faster attention.
Tips for Professional and Effective Communication
Here are some quick tips to ensure your contact with betechit.com is productive:
Be concise but thorough
Avoid aggressive or emotional language
Clearly state your expected outcome
Use bullet points for clarity
Include “Follow-Up” in the subject line after a few days
Professionalism can be the difference between silence and solution.
Is There a Phone Number for betechit.com Contacts?
While many platforms provide phone support, others prefer online communication to manage volume. If betechit.com offers a phone number:
Ensure it’s from their official site
Note business hours and time zones
Be prepared with account details and a clear issue summary
If no number is listed, stick to email or live chat options.
Using Whois and Domain Lookup for Contact Info
In rare cases where no contact options are visible, you can look up the domain registration using WHOIS tools. This can provide:
Registrant email (often protected by privacy services)
Hosting provider contact
Domain creation and expiry dates
While not ideal, this method can provide clues in urgent or legal situations.
Common Issues People Contact betechit.com About
Though it depends on the nature of the website, common inquiries might include:
Accessing locked or hacked accounts
Reporting bugs or errors
Requesting refunds or cancellations
Clarifying services or terms
Business collaboration proposals
Content removal or takedown requests
Knowing where your issue fits can help direct it to the correct team.
Staying Safe When Contacting Online Platforms
Before providing personal information, always confirm:
You are on the official website
The email address ends with the correct domain (e.g., @betechit.com)
The SSL certificate is valid (look for HTTPS)
You’re not on a phishing or fake clone site
Scammers often pose as support agents—verify before trusting.
Building Long-Term Partnerships with betechit.com
If you’re a business, creator, or developer looking to collaborate, contacting betechit.com with a well-prepared proposal is essential. Your message should include:
A brief about you or your company
How the partnership benefits both parties
Clear deliverables or objectives
Your contact details and past work (if relevant)
Such professional outreach can lead to joint ventures, affiliate programs, or content collaboration.
What to Do If You Get No Response
If you’ve contacted betechit.com and received no response:
Double-check the contact details
Follow up with a polite reminder after 2–3 days
Try a different method (e.g., social media)
Look for community forums or public discussion spaces
Escalate only if necessary (e.g., filing a complaint)
Persistence often pays off, especially if your inquiry is respectful and clear.
Alternatives to Direct Contact
If you’re unable to reach betechit.com directly, consider these alternatives:
Online forums discussing the platform
Reddit or Quora discussions
Reviews on Trustpilot or SiteJabber
Social media hashtags for shared user experience
These platforms can offer community-based advice while you await an official response.
Conclusion
Contacting betechit.com doesn’t have to be a mystery. Whether you’re seeking support, business opportunities, or technical help, there are numerous legitimate channels at your disposal—from email and contact forms to social media and live chat. Knowing how to reach out professionally and effectively will improve your chances of getting a prompt and helpful reply. As with any online interaction, staying polite, detailed, and vigilant is key to success.
ALSO READ:Why Monitor Out and Main Out: Key Differences and Best Uses
FAQs
Is there a public email address for betechit.com contacts?
Check the official site’s footer, contact page, or legal section for a verified email address.
Can I contact betechit.com via social media?
Yes, if they maintain official accounts, you can send direct messages or comments for assistance.
What if betechit.com doesn’t respond to my message?
Follow up after a few days, try alternate methods like social media, or check community forums for help.
Are contact forms on betechit.com safe to use?
Yes, as long as you’re on the official site with HTTPS encryption, your data should be secure.
Can I get phone support from betechit.com?
That depends on whether they publish a phone number. Most tech platforms prioritize email and chat support.
TECHNOLOGY
Cookie Clicker Unblocked: The Ultimate Guide
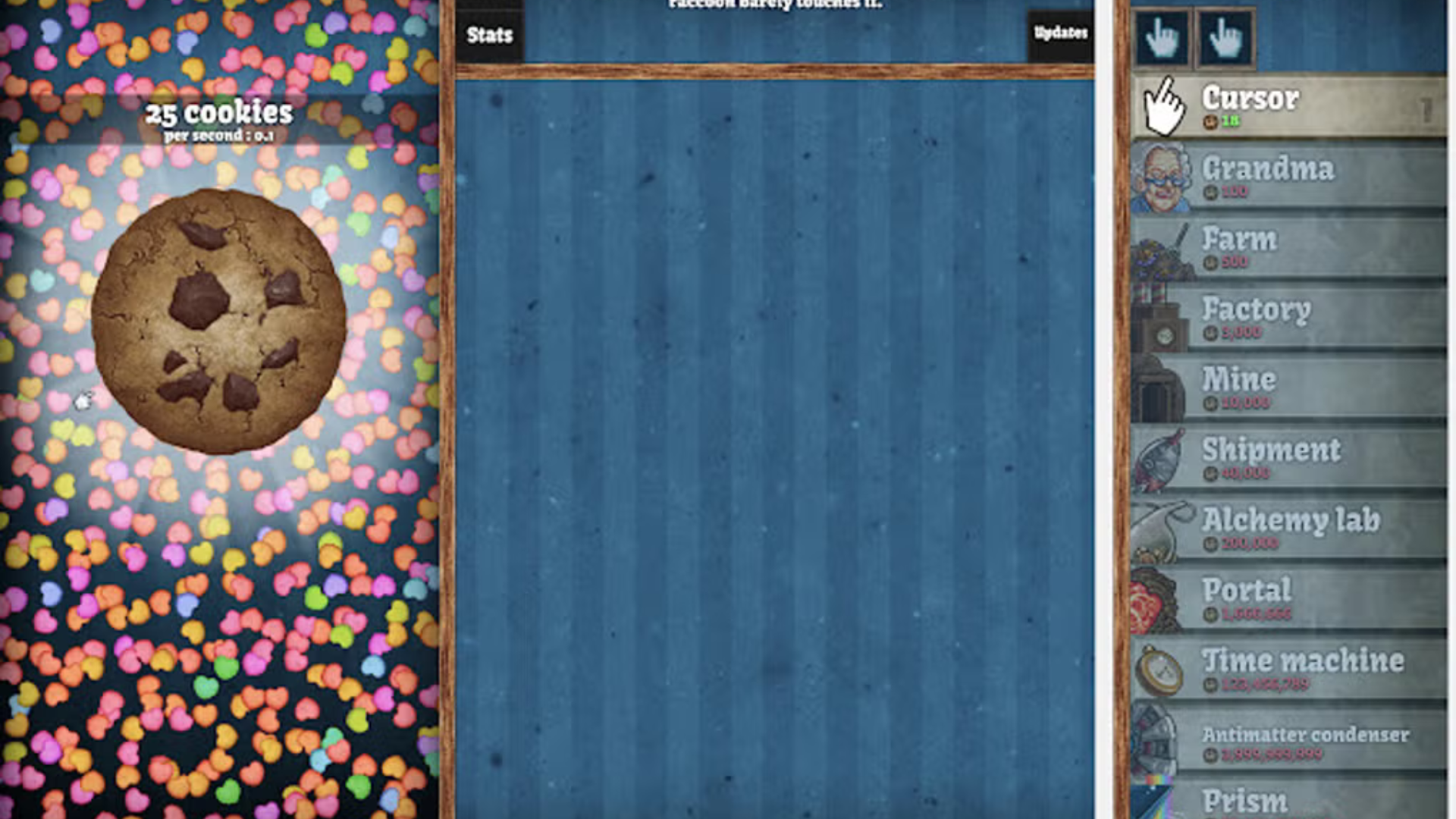
Many players enjoy playing Cookie Clicker during breaks or in their free time, but restrictions at school, work, or other locations can often prevent access. Some networks block gaming sites or specific content, leaving you unable to enjoy the game you love. That’s where unblocking comes in.
Playing Cookie Clicker unblocked means you can bypass these restrictions and access the game on any device, regardless of network limitations. Unblocked versions of the game are typically hosted on platforms that are not blocked by firewalls, enabling you to play Cookie Clicker without worrying about restrictions.
The main reasons people seek out unblocked versions of Cookie Clicker include:
Accessibility: Many schools, colleges, and workplaces block gaming sites, but unblocked versions can bypass these restrictions, letting you play whenever you want.
No Ads or Interruptions: Some official versions of Cookie Clicker feature ads or other interruptions, which can disrupt gameplay. Unblocked versions often provide an ad-free experience.
Play Anywhere, Anytime: Unblocked versions of the game allow you to enjoy Cookie Clicker on any device, whether it’s a school computer, a work laptop, or a personal device connected to a network with restrictions.
How to Play Cookie Clicker Unblocked
Playing Cookie Clicker unblocked is relatively simple, but there are a few different methods you can use, depending on where you are trying to access the game. Below are the most common ways to play Cookie Clicker unblocked.
1. Use Unblocked Game Websites
Several websites host unblocked versions of Cookie Clicker, making it easy to access the game from any device. These websites often host games that are not accessible through typical school or work networks. A quick search for “Cookie Clicker unblocked” will lead you to multiple sites where you can play the game without restrictions.
Some popular unblocked game websites include:
Unblocked Games 76
Unblocked Games 77
Google Sites (Custom Game Hosting)
By visiting these sites, you can play Cookie Clicker without encountering the usual network blocks. However, be cautious when choosing a website, as some may contain pop-up ads or other interruptions. It’s important to make sure the site is reputable and secure before playing.
2. Download a Browser Extension
Another way to play Cookie Clicker unblocked is by using a browser extension or add-on that can bypass network restrictions. Extensions like “Hola VPN” or “Proxmate” allow you to connect to servers in different locations, bypassing firewalls and network restrictions. By using these tools, you can access websites like Cookie Clicker without being stopped by filters.
3. Use a Proxy Server
If you prefer not to use extensions, you can also use a proxy server to access Cookie Clicker unblocked. A proxy server acts as an intermediary between your device and the internet, routing your traffic through a different server location to bypass restrictions. Websites like Hide.me and ProxySite offer free proxy services that can help you unblock gaming websites and access Cookie Clicker without limitations.
4. Use the Mobile Version
If you’re unable to access Cookie Clicker through a computer network, you can always download the mobile version of the game. Available for both iOS and Android devices, the mobile version of Cookie Clicker allows you to enjoy the game without worrying about restrictions. This is an excellent option if you’re on the go and want to play the game without being tied to a network.
Tips for Maximizing Your Cookie Clicker Experience
Once you have access to Cookie Clicker unblocked, you’ll want to make the most of your gameplay. Here are some tips to help you level up your cookie empire and progress faster.
1. Focus on Upgrades Early On
In the early stages of the game, it’s crucial to focus on upgrading your clicking power and unlocking new types of production units. Grandmas and farms are some of the first upgrades you’ll want to purchase, as they help automate the cookie production process, allowing you to earn more cookies with less effort.
2. Don’t Forget About Achievements
Cookie Clicker features various achievements that offer valuable bonuses, such as increased cookie production or extra cookies upon ascension. Keep an eye out for achievements and aim to unlock them as you play. They can significantly boost your progress in the game.
3. Consider Ascending
As you reach certain milestones, you’ll have the option to “ascend” in Cookie Clicker, which resets the game but gives you heavenly chips that provide permanent bonuses. While this may seem counterproductive, ascending helps you progress faster in the long run and unlock more powerful upgrades. Be strategic about when to ascend to maximize your benefits.
4. Experiment with Special Events
Cookie Clicker regularly features special in-game events, such as seasonal themes or limited-time upgrades. These events can provide valuable rewards, such as extra cookies or unique bonuses. Be sure to check in during these events to take advantage of special offers and boosts.
The Addictive Nature of Cookie Clicker
One of the key reasons Cookie Clicker has become so popular is its highly addictive gameplay loop. The game is designed to be simple yet rewarding, with constant progression and new upgrades to unlock. As you click and watch your cookie production grow, it creates a sense of accomplishment and satisfaction that keeps players coming back for more.
Cookie Clicker is a perfect example of the idle genre, where the gameplay is passive yet engaging. Players don’t need to be constantly active, but they can still watch their cookie empire grow and improve over time. This unique blend of relaxation and progression is what makes the game so captivating.
Conclusion
Cookie Clicker is an incredibly addictive game that has captivated players for years with its simple yet rewarding gameplay loop. By playing Cookie Clicker unblocked, you can bypass network restrictions and enjoy the game anytime, anywhere, without limitations. Whether you’re playing during a break at school or sneaking in some fun at work, unblocking the game opens up endless possibilities for cookie-clicking fun.
If you’re new to the game, remember to focus on upgrades, achievements, and strategic ascension to progress faster. With these tips in mind, you’ll be well on your way to building a cookie empire that will keep you hooked for hours on end.
ALSO READ:Understanding “RIF Error Forbidden”: Causes and Solutions
FAQs
What is Cookie Clicker?
Cookie Clicker is an idle game where players click a giant cookie to earn cookies, which are used to purchase upgrades and automate production.
How can I play Cookie Clicker unblocked?
You can play Cookie Clicker unblocked by visiting unblocked game websites, using a browser extension, or using a proxy server.
Is Cookie Clicker free to play?
Yes, Cookie Clicker is free to play, and you can access it on various platforms, including browsers and mobile devices.
What are some tips for playing Cookie Clicker?
Focus on upgrading your clicking power, unlocking achievements, and considering ascension to boost your progress.
Why is Cookie Clicker so addictive?
Cookie Clicker’s addictive nature comes from its rewarding gameplay loop, constant progression, and the sense of accomplishment as you expand your cookie empire.
TECHNOLOGY
How Unreal Engine Game Development Companies Are Shaping the Future of Gaming

The gaming industry is experiencing rapid evolution, driven by technological advancements and changing consumer expectations. At the forefront of this transformation are Unreal Engine game development companies, which are leveraging the power of Unreal Engine to create next-generation gaming experiences. This article analyzes the pivotal role these companies play in advancing gaming technologies and shaping the future of the industry.
Advancing Graphics and Visual Fidelity
Unreal Engine is renowned for its cutting-edge graphics capabilities, allowing developers to create visually stunning and immersive environments. With features like Nanite and Lumen, an unreal engine game development company can enable real-time rendering of high-fidelity graphics and dynamic lighting, setting a new standard for visual quality in games. Companies such as N-iX Games and Game-Ace are utilizing these advanced tools to push the boundaries of what is possible in game design, resulting in experiences that captivate players and enhance storytelling.

Enhancing Gameplay Mechanics
Unreal Engine’s robust toolset allows developers to implement complex gameplay mechanics with ease. The Blueprint visual scripting system simplifies the process of creating interactive elements without extensive coding knowledge, making it accessible for a wider range of developers. This democratization of game development enables smaller studios to experiment with innovative gameplay concepts that can lead to groundbreaking titles. By fostering creativity and experimentation, Unreal Engine game development companies are driving the evolution of gameplay mechanics across the industry.
Supporting Cross-Platform Development
As gaming becomes increasingly diverse, cross-platform compatibility has become essential for reaching broader audiences. Unreal Engine provides a seamless solution for developing games that can be played across multiple platforms, including PC, consoles, and mobile devices. This capability allows developers to maximize their reach without compromising on quality or performance. Companies like Innowise leverage Unreal Engine’s cross-platform capabilities to ensure that their games deliver consistent experiences regardless of the device, thus enhancing player engagement and satisfaction.
Facilitating Virtual Reality Experiences
The rise of virtual reality (VR) has opened new avenues for immersive gaming experiences. Unreal Engine is a leading platform for VR development, offering tools that enable developers to create engaging virtual environments that feel lifelike. Unreal game development companies are at the forefront of this trend, creating VR titles that transport players into entirely new worlds. By harnessing the power of Unreal Engine, these companies are not only enhancing traditional gaming but also pioneering new forms of interactive entertainment.
Streamlining Development Processes
Unreal Engine game development companies benefit from a full-cycle development approach that streamlines the entire process—from concept to launch. This efficiency is crucial in an industry where time-to-market can determine success. By utilizing Unreal Engine’s comprehensive suite of tools, these companies can reduce development time while maintaining high-quality standards. This capability allows them to respond quickly to market demands and trends, ensuring that their games remain relevant and competitive.
Building Communities Around Games
Unreal Engine game development companies often engage with their player communities through feedback loops and collaborative initiatives. By involving players in the development process, these companies can create games that resonate more deeply with their audiences. Community-driven development not only enhances player satisfaction but also fosters loyalty and engagement, which are vital for long-term success in the gaming industry.
Conclusion
Unreal Engine game development companies are playing a transformative role in shaping the future of gaming by leveraging advanced technology, enhancing gameplay mechanics, supporting cross-platform development, facilitating VR experiences, streamlining processes, and building strong communities around their games. As these companies continue to innovate and push boundaries, they will undoubtedly drive the evolution of gaming into new realms of creativity and interactivity. The future looks bright for both developers and players alike as they explore the limitless possibilities offered by Unreal Engine and its dedicated game development studios.

 Cartoon1 year ago
Cartoon1 year agoUnlocking the Potential of Nekopoi.care: A Comprehensive Guide

 Game1 year ago
Game1 year agoExploring Aopickleballthietke.com: Your Ultimate Pickleball Destination

 BUSINESS1 year ago
BUSINESS1 year agoWhat Companies Are In The Consumer Services Field

 BUSINESS12 months ago
BUSINESS12 months agoUnraveling the Mystery of 405 Howard Street San Francisco charge on Credit Card

 HOME IMPROVEMENT1 year ago
HOME IMPROVEMENT1 year agoVtrahe vs. Other Platforms: Which One Reigns Supreme?

 TECHNOLOGY1 year ago
TECHNOLOGY1 year agoThe Guide to Using Anon Vault for Secure Data Storage

 ENTERTAINMENT9 months ago
ENTERTAINMENT9 months agoUnderstanding Bunkr Album: A Comprehensive Guide

 ENTERTAINMENT1 year ago
ENTERTAINMENT1 year agoThe Epic Return: Revenge of the Iron-Blooded Sword Hound
















