TECHNOLOGY
The Cosmos of Cybersecurity: A Detailed Write-Up on Aliens HTB

In the ever-evolving landscape of cybersecurity, Hack The Box (HTB) stands out as a premier platform for both budding and seasoned penetration testers. Among its diverse array of challenges, the “Aliens” machine offers a compelling and educational experience. This write-up provides an in-depth exploration of the Aliens HTB challenge, breaking down the key phases of the penetration testing process and offering insights into the techniques used to conquer this intriguing exercise.
Understanding Aliens HTB
The Aliens machine on Hack The Box is designed to simulate a real-world vulnerable environment, providing a medium-level challenge for penetration testers. The challenge revolves around exploiting vulnerabilities in a controlled setting to gain unauthorized access and capture the flag (CTF), which is a common goal in cybersecurity exercises. The Aliens HTB machine is structured to teach and test various skills, from initial reconnaissance to privilege escalation.
Objective
The core objectives of the Aliens HTB challenge are:
- Reconnaissance: Gather information about the target machine to identify potential points of entry.
- Vulnerability Assessment: Discover and analyze vulnerabilities within the services and applications running on the machine.
- Exploitation: Use identified vulnerabilities to gain access to the system.
- Privilege Escalation: Elevate privileges to gain higher-level access on the machine.
- Flag Retrieval: Locate and extract the flag file, which represents the successful completion of the challenge.
Initial Reconnaissance
Reconnaissance is the first and crucial phase in penetration testing. It involves gathering as much information as possible about the target machine to identify vulnerabilities and potential entry points.
Port Scanning
The initial step in reconnaissance is to perform a port scan. This involves identifying open ports and the services running on them. By examining which ports are open, you can infer the types of services and applications that may be present on the machine. For instance, open ports might indicate the presence of a web server, database server, or other network services.
Service Enumeration
Following port scanning, the next step is service enumeration. This process involves probing the identified services to gather detailed information about their versions and configurations. Service enumeration helps in identifying specific vulnerabilities associated with the versions of the services running on the target machine. For example, if a web server is running, you might look for specific configurations or known vulnerabilities related to that server.
Vulnerability Identification
With information from reconnaissance in hand, the next phase is to identify vulnerabilities within the services and applications running on the machine. This involves:
Researching Known Vulnerabilities
Once you have information about the services and their versions, you can research known vulnerabilities related to those versions. Vulnerability databases and resources like security advisories can provide insights into common vulnerabilities associated with specific software versions.
Assessing Configuration and Security Practices
In addition to known vulnerabilities, it’s also important to assess the configuration and security practices of the services. Misconfigurations, such as overly permissive file permissions or weak authentication mechanisms, can also present security risks.
Exploitation
Exploitation is the phase where identified vulnerabilities are leveraged to gain access to the target machine. This involves:
Exploiting Web Servers
If the target machine has a web server running, common exploitation techniques might include:
- Directory Traversal: Accessing files and directories that are not intended to be exposed through web requests.
- File Upload Vulnerabilities: Uploading malicious files to gain unauthorized access or execute code on the server.
Exploiting Databases
For database servers, SQL injection attacks might be used to manipulate the database or extract sensitive information. SQL injection can allow an attacker to execute arbitrary SQL queries, which can lead to unauthorized access or data extraction.
Privilege Escalation
Once access is gained, the next step is privilege escalation, which involves elevating your access level to gain more control over the machine. This might include:
Finding and Exploiting Local Vulnerabilities
Privilege escalation often involves searching for local vulnerabilities or misconfigurations that can be exploited to gain higher-level access. This might include exploiting setuid binaries or other privileged processes.
Checking for Weak Permissions
Assessing file and directory permissions can reveal weaknesses that allow a user to gain elevated privileges. For example, if sensitive files or binaries have incorrect permissions, they might be exploited to escalate privileges.
Capturing the Flag
The final step in the challenge is to locate and retrieve the flag file. On most HTB machines, the flag file is located in a directory that requires elevated permissions to access. Common locations include:
- Root Directory: Typically accessible only by the root user.
- Home Directories: Often found in the home directory of a user with elevated privileges.
Once the flag file is located, it can be read to complete the challenge and prove successful exploitation of the machine.
Exploitation Process Overview
Step | Description | Purpose |
| Initial Reconnaissance | Identify open ports and running services | Gather information about the target machine |
| Vulnerability Identification | Research and assess vulnerabilities in services or configurations | Find weaknesses to exploit |
| Exploitation | Leverage vulnerabilities to gain access | Achieve initial access to the machine |
| Privilege Escalation | Increase access level to gain higher-level permissions | Obtain full control of the machine |
| Capture the Flag | Locate and retrieve the flag file | Complete the challenge |
Conclusion
The Aliens HTB challenge offers a comprehensive and practical learning experience in the field of penetration testing and cybersecurity. By engaging in this exercise, participants gain hands-on experience with various aspects of ethical hacking, including reconnaissance, vulnerability identification, exploitation, and privilege escalation. The insights and skills acquired from tackling the Aliens machine are invaluable for anyone looking to advance their knowledge and expertise in cybersecurity.
As the digital landscape continues to evolve, challenges like Aliens provide a crucial platform for developing and honing penetration testing skills. By embracing these challenges, cybersecurity professionals and enthusiasts can stay ahead of emerging threats and contribute to a safer and more secure digital environment.
FAQs
1. What is the Aliens HTB challenge, and what is its purpose?
Aliens is a penetration testing challenge on Hack The Box (HTB) designed to simulate a vulnerable environment that testers need to exploit. The challenge’s purpose is to provide a practical learning experience in ethical hacking by guiding participants through the processes of reconnaissance, vulnerability assessment, exploitation, privilege escalation, and flag retrieval. It is categorized as a medium difficulty machine, making it suitable for those with some prior experience in penetration testing.
2. What skills or knowledge are required to successfully complete the Aliens HTB challenge?
To successfully complete the Aliens HTB challenge, participants should have:
- Basic Knowledge of Networking and Protocols: Understanding of TCP/IP, common ports, and network services.
- Proficiency in Penetration Testing Techniques: Familiarity with tools and techniques for scanning, enumeration, and exploitation.
- Experience with Web and Database Vulnerabilities: Knowledge of common vulnerabilities such as SQL injection, directory traversal, and file upload issues.
- Skills in Privilege Escalation: Ability to identify and exploit local vulnerabilities to gain elevated privileges on a system.
3. How do I start with the Aliens HTB challenge?
To start with the Aliens HTB challenge, follow these steps:
- Access the HTB Platform: Log in to your Hack The Box account and locate the Aliens machine in the challenges section.
- Perform Reconnaissance: Begin by scanning the machine to identify open ports and services.
- Enumerate Services: Gather detailed information about the services and applications running on the machine.
- Identify Vulnerabilities: Research and assess potential vulnerabilities in the identified services.
- Exploit Vulnerabilities: Use the discovered vulnerabilities to gain initial access to the machine.
- Escalate Privileges: Increase your access level to gain full control of the machine.
- Capture the Flag: Locate and retrieve the flag file to complete the challenge.
4. What tools are commonly used in the Aliens HTB challenge?
Several tools are commonly used for different phases of the Aliens HTB challenge, including:
- Nmap: For port scanning and service enumeration.
- Nikto or Dirb: For web application scanning and directory enumeration.
- SearchSploit: For researching known vulnerabilities related to specific software versions.
- Burp Suite: For advanced web application testing and vulnerability scanning.
- LinPEAS or similar tools: For local privilege escalation enumeration on Linux systems.
5. What should I do if I get stuck during the Aliens HTB challenge?
If you encounter difficulties while working on the Aliens HTB challenge, consider the following approaches:
- Review Documentation: Revisit any documentation or hints provided within the HTB platform.
- Research: Look up information on vulnerabilities, tools, and techniques that may be relevant to the challenge.
- Community Forums: Engage with the HTB community forums or Discord channels for advice or hints.
- Methodical Approach: Re-evaluate your approach to reconnaissance, enumeration, and exploitation to ensure you haven’t missed any crucial steps.
- Practice and Learn: Use the challenge as an opportunity to practice and learn, and revisit areas where you may need additional training or experience.
TECHNOLOGY
Cookie Clicker Unblocked: The Ultimate Guide
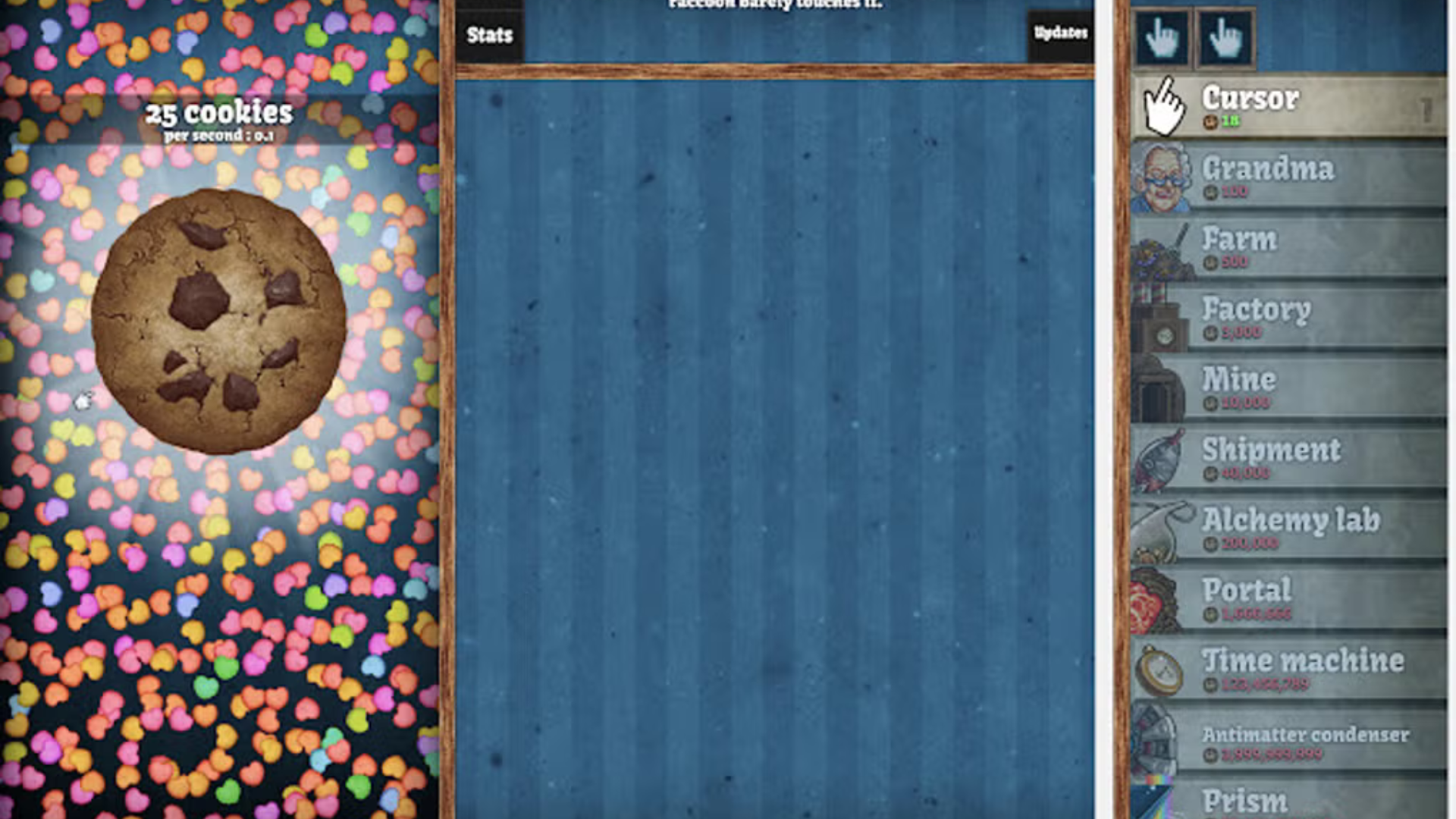
Many players enjoy playing Cookie Clicker during breaks or in their free time, but restrictions at school, work, or other locations can often prevent access. Some networks block gaming sites or specific content, leaving you unable to enjoy the game you love. That’s where unblocking comes in.
Playing Cookie Clicker unblocked means you can bypass these restrictions and access the game on any device, regardless of network limitations. Unblocked versions of the game are typically hosted on platforms that are not blocked by firewalls, enabling you to play Cookie Clicker without worrying about restrictions.
The main reasons people seek out unblocked versions of Cookie Clicker include:
Accessibility: Many schools, colleges, and workplaces block gaming sites, but unblocked versions can bypass these restrictions, letting you play whenever you want.
No Ads or Interruptions: Some official versions of Cookie Clicker feature ads or other interruptions, which can disrupt gameplay. Unblocked versions often provide an ad-free experience.
Play Anywhere, Anytime: Unblocked versions of the game allow you to enjoy Cookie Clicker on any device, whether it’s a school computer, a work laptop, or a personal device connected to a network with restrictions.
How to Play Cookie Clicker Unblocked
Playing Cookie Clicker unblocked is relatively simple, but there are a few different methods you can use, depending on where you are trying to access the game. Below are the most common ways to play Cookie Clicker unblocked.
1. Use Unblocked Game Websites
Several websites host unblocked versions of Cookie Clicker, making it easy to access the game from any device. These websites often host games that are not accessible through typical school or work networks. A quick search for “Cookie Clicker unblocked” will lead you to multiple sites where you can play the game without restrictions.
Some popular unblocked game websites include:
Unblocked Games 76
Unblocked Games 77
Google Sites (Custom Game Hosting)
By visiting these sites, you can play Cookie Clicker without encountering the usual network blocks. However, be cautious when choosing a website, as some may contain pop-up ads or other interruptions. It’s important to make sure the site is reputable and secure before playing.
2. Download a Browser Extension
Another way to play Cookie Clicker unblocked is by using a browser extension or add-on that can bypass network restrictions. Extensions like “Hola VPN” or “Proxmate” allow you to connect to servers in different locations, bypassing firewalls and network restrictions. By using these tools, you can access websites like Cookie Clicker without being stopped by filters.
3. Use a Proxy Server
If you prefer not to use extensions, you can also use a proxy server to access Cookie Clicker unblocked. A proxy server acts as an intermediary between your device and the internet, routing your traffic through a different server location to bypass restrictions. Websites like Hide.me and ProxySite offer free proxy services that can help you unblock gaming websites and access Cookie Clicker without limitations.
4. Use the Mobile Version
If you’re unable to access Cookie Clicker through a computer network, you can always download the mobile version of the game. Available for both iOS and Android devices, the mobile version of Cookie Clicker allows you to enjoy the game without worrying about restrictions. This is an excellent option if you’re on the go and want to play the game without being tied to a network.
Tips for Maximizing Your Cookie Clicker Experience
Once you have access to Cookie Clicker unblocked, you’ll want to make the most of your gameplay. Here are some tips to help you level up your cookie empire and progress faster.
1. Focus on Upgrades Early On
In the early stages of the game, it’s crucial to focus on upgrading your clicking power and unlocking new types of production units. Grandmas and farms are some of the first upgrades you’ll want to purchase, as they help automate the cookie production process, allowing you to earn more cookies with less effort.
2. Don’t Forget About Achievements
Cookie Clicker features various achievements that offer valuable bonuses, such as increased cookie production or extra cookies upon ascension. Keep an eye out for achievements and aim to unlock them as you play. They can significantly boost your progress in the game.
3. Consider Ascending
As you reach certain milestones, you’ll have the option to “ascend” in Cookie Clicker, which resets the game but gives you heavenly chips that provide permanent bonuses. While this may seem counterproductive, ascending helps you progress faster in the long run and unlock more powerful upgrades. Be strategic about when to ascend to maximize your benefits.
4. Experiment with Special Events
Cookie Clicker regularly features special in-game events, such as seasonal themes or limited-time upgrades. These events can provide valuable rewards, such as extra cookies or unique bonuses. Be sure to check in during these events to take advantage of special offers and boosts.
The Addictive Nature of Cookie Clicker
One of the key reasons Cookie Clicker has become so popular is its highly addictive gameplay loop. The game is designed to be simple yet rewarding, with constant progression and new upgrades to unlock. As you click and watch your cookie production grow, it creates a sense of accomplishment and satisfaction that keeps players coming back for more.
Cookie Clicker is a perfect example of the idle genre, where the gameplay is passive yet engaging. Players don’t need to be constantly active, but they can still watch their cookie empire grow and improve over time. This unique blend of relaxation and progression is what makes the game so captivating.
Conclusion
Cookie Clicker is an incredibly addictive game that has captivated players for years with its simple yet rewarding gameplay loop. By playing Cookie Clicker unblocked, you can bypass network restrictions and enjoy the game anytime, anywhere, without limitations. Whether you’re playing during a break at school or sneaking in some fun at work, unblocking the game opens up endless possibilities for cookie-clicking fun.
If you’re new to the game, remember to focus on upgrades, achievements, and strategic ascension to progress faster. With these tips in mind, you’ll be well on your way to building a cookie empire that will keep you hooked for hours on end.
ALSO READ:Understanding “RIF Error Forbidden”: Causes and Solutions
FAQs
What is Cookie Clicker?
Cookie Clicker is an idle game where players click a giant cookie to earn cookies, which are used to purchase upgrades and automate production.
How can I play Cookie Clicker unblocked?
You can play Cookie Clicker unblocked by visiting unblocked game websites, using a browser extension, or using a proxy server.
Is Cookie Clicker free to play?
Yes, Cookie Clicker is free to play, and you can access it on various platforms, including browsers and mobile devices.
What are some tips for playing Cookie Clicker?
Focus on upgrading your clicking power, unlocking achievements, and considering ascension to boost your progress.
Why is Cookie Clicker so addictive?
Cookie Clicker’s addictive nature comes from its rewarding gameplay loop, constant progression, and the sense of accomplishment as you expand your cookie empire.
TECHNOLOGY
How Unreal Engine Game Development Companies Are Shaping the Future of Gaming

The gaming industry is experiencing rapid evolution, driven by technological advancements and changing consumer expectations. At the forefront of this transformation are Unreal Engine game development companies, which are leveraging the power of Unreal Engine to create next-generation gaming experiences. This article analyzes the pivotal role these companies play in advancing gaming technologies and shaping the future of the industry.
Advancing Graphics and Visual Fidelity
Unreal Engine is renowned for its cutting-edge graphics capabilities, allowing developers to create visually stunning and immersive environments. With features like Nanite and Lumen, an unreal engine game development company can enable real-time rendering of high-fidelity graphics and dynamic lighting, setting a new standard for visual quality in games. Companies such as N-iX Games and Game-Ace are utilizing these advanced tools to push the boundaries of what is possible in game design, resulting in experiences that captivate players and enhance storytelling.

Enhancing Gameplay Mechanics
Unreal Engine’s robust toolset allows developers to implement complex gameplay mechanics with ease. The Blueprint visual scripting system simplifies the process of creating interactive elements without extensive coding knowledge, making it accessible for a wider range of developers. This democratization of game development enables smaller studios to experiment with innovative gameplay concepts that can lead to groundbreaking titles. By fostering creativity and experimentation, Unreal Engine game development companies are driving the evolution of gameplay mechanics across the industry.
Supporting Cross-Platform Development
As gaming becomes increasingly diverse, cross-platform compatibility has become essential for reaching broader audiences. Unreal Engine provides a seamless solution for developing games that can be played across multiple platforms, including PC, consoles, and mobile devices. This capability allows developers to maximize their reach without compromising on quality or performance. Companies like Innowise leverage Unreal Engine’s cross-platform capabilities to ensure that their games deliver consistent experiences regardless of the device, thus enhancing player engagement and satisfaction.
Facilitating Virtual Reality Experiences
The rise of virtual reality (VR) has opened new avenues for immersive gaming experiences. Unreal Engine is a leading platform for VR development, offering tools that enable developers to create engaging virtual environments that feel lifelike. Unreal game development companies are at the forefront of this trend, creating VR titles that transport players into entirely new worlds. By harnessing the power of Unreal Engine, these companies are not only enhancing traditional gaming but also pioneering new forms of interactive entertainment.
Streamlining Development Processes
Unreal Engine game development companies benefit from a full-cycle development approach that streamlines the entire process—from concept to launch. This efficiency is crucial in an industry where time-to-market can determine success. By utilizing Unreal Engine’s comprehensive suite of tools, these companies can reduce development time while maintaining high-quality standards. This capability allows them to respond quickly to market demands and trends, ensuring that their games remain relevant and competitive.
Building Communities Around Games
Unreal Engine game development companies often engage with their player communities through feedback loops and collaborative initiatives. By involving players in the development process, these companies can create games that resonate more deeply with their audiences. Community-driven development not only enhances player satisfaction but also fosters loyalty and engagement, which are vital for long-term success in the gaming industry.
Conclusion
Unreal Engine game development companies are playing a transformative role in shaping the future of gaming by leveraging advanced technology, enhancing gameplay mechanics, supporting cross-platform development, facilitating VR experiences, streamlining processes, and building strong communities around their games. As these companies continue to innovate and push boundaries, they will undoubtedly drive the evolution of gaming into new realms of creativity and interactivity. The future looks bright for both developers and players alike as they explore the limitless possibilities offered by Unreal Engine and its dedicated game development studios.
TECHNOLOGY
The Future of Sustainable Luxury: How Brands Are Changing the Game

Luxury has long been associated with exclusivity, craftsmanship, and indulgence. However, in today’s world, consumers are demanding more than just opulence—they want sustainability, ethical sourcing, and transparency. High-end brands are responding by redefining what it means to be luxurious, embracing eco-friendly materials, circular fashion, and responsible production methods. The shift toward sustainable luxury is not just a passing trend but a necessity for the future of the industry.
The Rise of Conscious Consumers
Today’s luxury consumers are more informed and environmentally conscious than ever before. They seek products that align with their values, making sustainability a key purchasing factor. According to a 2023 Bain & Company report, 60% of luxury shoppers consider a brand’s sustainability efforts before making a purchase. To appeal to this evolving market, brands are leveraging innovative materials and ethical labor practices. Some are even using an AI image generator to create digital prototypes, reducing waste in the design process while maintaining creative freedom.
Eco-Friendly Materials and Ethical Sourcing
Luxury brands are moving away from traditional resource-intensive materials and adopting sustainable alternatives. Organic cotton, recycled metals, lab-grown diamonds, and plant-based leather are becoming the new standard. For example, Stella McCartney has pioneered the use of Mylo, a mushroom-based leather alternative that replicates the texture and durability of traditional leather without harming animals or the environment.
Ethical sourcing is also a major focus. Brands like Chopard have committed to using 100% ethical gold, ensuring that their materials are responsibly mined and traceable. Similarly, luxury watchmakers such as Panerai are incorporating recycled titanium and ocean-sourced plastics into their designs, proving that sustainability and luxury can coexist.
Circular Fashion and Upcycling
The traditional fashion industry follows a linear model: make, sell, use, and discard. However, sustainable luxury is shifting toward a circular economy, where products are designed for longevity, repairability, and recyclability.
High-end labels are embracing upcycling—reusing old materials to create new, high-quality pieces. Brands like Gucci and Louis Vuitton have launched upcycled collections that breathe new life into surplus fabrics and vintage designs. Additionally, resale platforms like The RealReal and Vestiaire Collective are thriving, allowing consumers to buy and sell pre-owned luxury goods, extending the lifespan of premium products while reducing environmental impact.
Low-Impact Manufacturing and Carbon Neutrality
Luxury brands are also rethinking their production methods to reduce their carbon footprint. Many are shifting toward carbon-neutral manufacturing, investing in renewable energy, and using water-saving techniques.
For example, Kering—the parent company of brands like Balenciaga and Bottega Veneta—has pledged to reduce its greenhouse gas emissions by 40% by 2035. Similarly, LVMH has introduced sustainable packaging solutions and reduced plastic use across its product lines. The goal is not just to reduce environmental harm but also to set new standards for the entire industry.
Sustainable Luxury in the Automotive and Hospitality Sectors
Sustainability is not limited to fashion; it’s transforming the entire luxury sector, including automobiles and hospitality. High-end car manufacturers like Bentley and Rolls-Royce are investing in electric and hybrid models, reducing their reliance on fossil fuels without compromising performance or luxury.
The hospitality industry is also adopting eco-friendly practices. Luxury resorts such as Soneva and Six Senses prioritize sustainability by implementing renewable energy, zero-waste initiatives, and locally sourced materials. These brands are proving that luxury experiences don’t have to come at the expense of the environment.
The Role of Technology in Sustainable Luxury
Technology plays a crucial role in making sustainability more accessible in the luxury market. Digital fashion, blockchain authentication, and AI-driven production processes are revolutionizing the way brands operate.
Blockchain technology is particularly impactful in ensuring supply chain transparency. High-end brands can track the journey of their materials from source to final product, providing customers with proof of authenticity and ethical sourcing. Meanwhile, digital fashion allows consumers to experiment with high-end looks in the virtual world, reducing the need for physical production and minimizing waste.
The Future of Luxury: Sustainability as the Standard
The future of luxury lies in sustainability. As more brands commit to eco-conscious practices, the definition of opulence is shifting from excess to responsibility. Consumers now expect luxury products to not only be beautiful but also ethical and environmentally friendly.
By embracing sustainable materials, circular economy principles, and low-impact manufacturing, high-end brands are setting the stage for a greener, more responsible industry. As we move forward, sustainability won’t just be a trend in luxury—it will be the standard that defines it.
Luxury no longer has to be wasteful; it can be a force for good. And as brands continue to innovate, the future of sustainable luxury looks more promising than ever.

 Cartoon1 year ago
Cartoon1 year agoUnlocking the Potential of Nekopoi.care: A Comprehensive Guide

 Game1 year ago
Game1 year agoExploring Aopickleballthietke.com: Your Ultimate Pickleball Destination

 BUSINESS1 year ago
BUSINESS1 year agoWhat Companies Are In The Consumer Services Field

 BUSINESS12 months ago
BUSINESS12 months agoUnraveling the Mystery of 405 Howard Street San Francisco charge on Credit Card

 HOME IMPROVEMENT1 year ago
HOME IMPROVEMENT1 year agoVtrahe vs. Other Platforms: Which One Reigns Supreme?

 TECHNOLOGY12 months ago
TECHNOLOGY12 months agoThe Guide to Using Anon Vault for Secure Data Storage

 ENTERTAINMENT8 months ago
ENTERTAINMENT8 months agoUnderstanding Bunkr Album: A Comprehensive Guide

 ENTERTAINMENT1 year ago
ENTERTAINMENT1 year agoThe Epic Return: Revenge of the Iron-Blooded Sword Hound
















